Happy Clients
Projects Done
Hours Worked
Support Available

Strengthen your networks with our Cyber Security Services
With the increasing vulnerabilities on the Internet, cyber security has become a crucial part of the organization. The landscape of cyber threats increases with the massive shift of a technology. To make this easier, we have developed our brilliant cyber security services. We act as our client's reliable and trusted partner to keep their data secure with our expertise. Our consistent efforts and technology-driven approach help organization save their sensitive data from all kinds of cyber threats. We help organizations keep up with today's cyber threats' volume, sophistication, and pace. Our combined efforts prevent data breaches for organizations by applying advanced threat detection and response plans to block attacks before they damage your data privacy.
We help the organization leverage faster with our unified solutions to protect from vulnerabilities of the organization's environment. Drogenide Softwares allows organizations in the increasing landscape of cyber threats to provide them with the assistance they seek.
Network security
Our qualified professionals endeavor hard to make businesses safe from all types of cyber threats regarding cybersecurity. Our dedicated experts protect the networks from external threats such as intruders, targeted attackers, and malware. Our effective network security services control malicious programs and software to intrude on your systems. One of the most common examples of network security is firewalls, antivirus programs, antispyware programs, and continuous monitoring of internet access. Drogenide Softwares helps you adopt these technology changes with the proper guidance and focused efforts. That is why we act as the most trusted cyber security service providers for our clients.
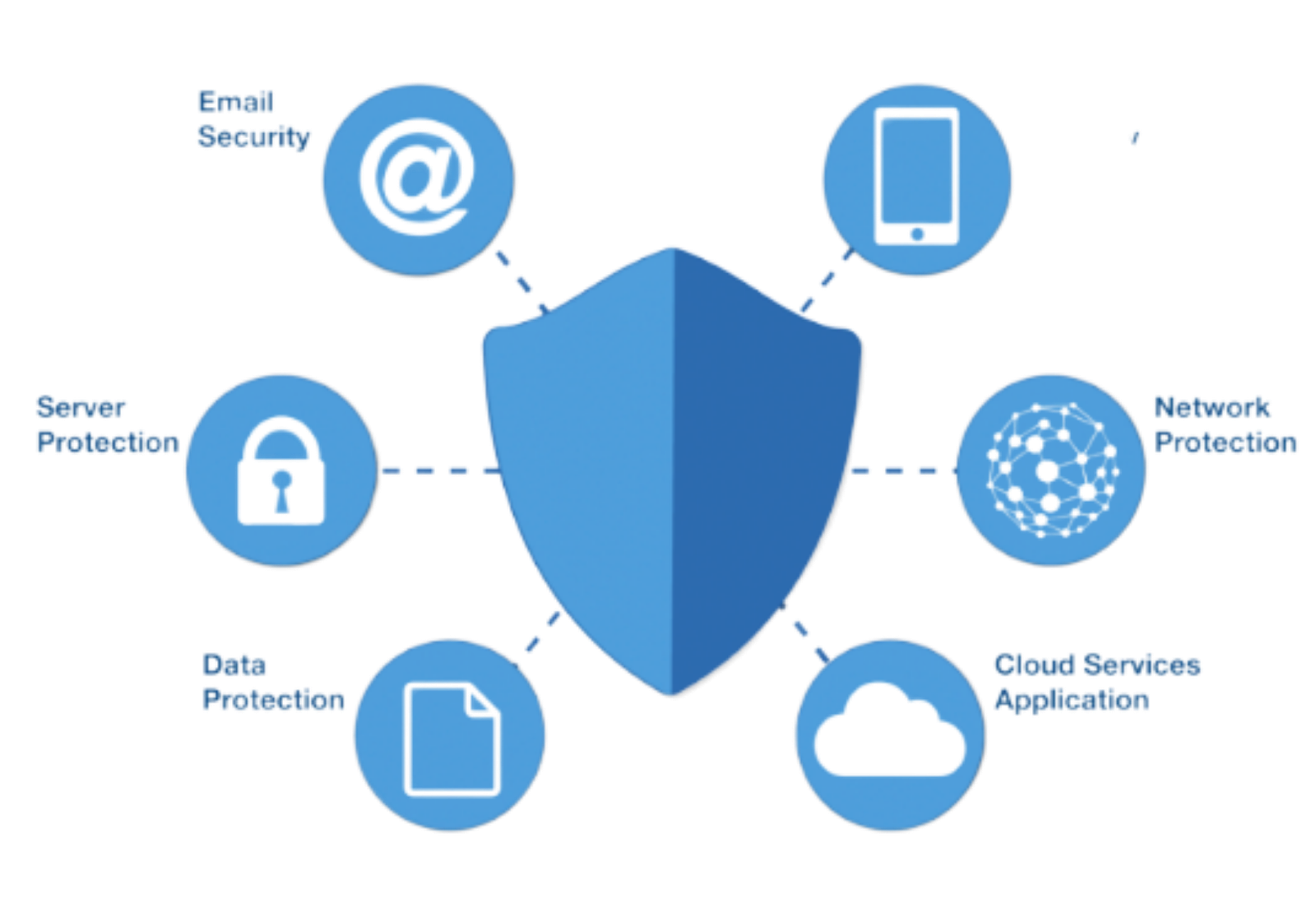
Types of Network security we provide:
Firewalls
The organizations extensively used traditional firewalls to control incoming and outgoing traffic on their servers for years. It is the most prominent part of network security. With the increasing threat landscapes in the network, the next-generation firewalls (NGFW) have become an integral part of security. These NGFWs use a comprehensive application-level inspection, intrusion prevention, and intelligence from the various sources outside the firewalls.
WAN and Branch protection
Organizations these days exchange large and important packets of data across the world to their partners, branch individuals, and other individuals. The branch office network security aims towards making the internet traffic safe among branches, corporate resources, and remote employees. With our consistent efforts and technology-driven solutions, we protect the organizations by keeping their sophisticated data packets safe from all kinds of the data breach.
Intrusion Prevention System security system
The intrusion prevention security system is based on identifying suspicious activities to detect and prevent them from attacking the organization's systems. The IPS initiates preventive steps to avoid possible threats to the systems by configuring other network security tools, adjusting corporate security policies to block employees or individuals engaging in the threats. We provide cohesive solutions to prevent all these suspicious activities.
Secure web gateway
A secure web gateway sits between all the incoming and outgoing traffic to prevent unauthorized and malicious traffic on the organization's networks. Several web security technologies, such as a web filter, are used to maintain a blacklist, block commonly exploited network ports by using the database of malicious websites to prevent the individuals from engaging in high-risk activities on the organization's network.

Cloud Security
Cloud storage is believed as the most secure platform to store your data. Nowadays, people hardly use their hard drives to store data, and everything is saved on the cloud servers of the users. The same happens with businesses. However, keeping your cloud servers secure is still essential due to the increasing threats. Our consistent efforts and technology-driven solutions help businesses to keep their cloud servers safe from all kinds of attacks as most of your business's activities depend on the cloud servers these days. Drogenide Softwares is here with our unparalleled cyber security services to serve you the best:
Types of Cloud Security we provide:
Identity and access management (IAM)
The identity and access management tools help businesses create a digital identity for the individuals accessing the organization's data to monitor and restrict them actively. It consists of all the individuals, processes, and systems to manage all the access to the various resources. The overall goal is to verify the identity of the organization. With Drogenide Softwares, you don't have to worry about the IAM services as we are here to provide you with one.
Data loss prevention
Data loss prevention services offer a set of tools that use a combination of remediation alerts, data encryption, and other preventive measures to secure the organization's data from losses. It refers to the monitoring, protecting, and verifying the data at rest, in motion, in the cloud, and on-premises. Our qualified team of experts can provide data loss prevention services to prevent your organization's networks from data breaches.
Security information and event management
The security information and event management system is a comprehensive solution to collect logs and events for automating threat monitoring, detection, and response in a cloud-based environment. It provides the IT teams the ability to track, monitor, and respond the potential threats. Protect the sophisticated data of your organization with our cohesive cyber security solutions for all types of vulnerabilities in the internet world.
Business continuity and disaster recovery
The business continuity and disaster recovery measures are implemented to ensure less interruption in the business operations. The overall goal is to provide a flexible and reliable solution for all types of service interruptions. It is a cloud-centric approach used to minimize costs and maximize the organizations' benefits. With Drogenide Softwares, you don't have to worry about disaster recovery as we master preventing data loss with our effective response plans.
Application Security
Applications are more vulnerable to cyberattacks due to the easy accessibility over various networks. The main motive behind application security is to keep the applications secure from threats. A secure application requires suitable applications security methods implemented at the development stage. Antivirus programs, firewalls, and encryptions programs are one such method to improve the security of your organization's data in applications. Drogenide Softwares is a one-stop solution for all your cybersecurity-related issues. Application security has become an unavoidable threat to organizations. And we are here to help you with that:
Types of Application security we provide:
Authentication
The authentication process is essential to making a secure application for the users. The authentication process ensures that the user trying to access is actually what he claims. Several methods, such as two-factor authentication, including username, password, email address, phone numbers, fingerprint, retina scans, and facial recognition, authenticate the login process. We provide robust application security to prevent all types of cyberattacks.
Authorization
The authorization step is crucial to saving the applications' data from unwarranted threats. The authorization process helps the systems identify whether the user's credentials match the authorized user's list. After the authentication process, the authorization step is a must to ensure that the user's data matches the list of the authorized users stored in the organization. With Drogenide Softwares, you get everything in a single platter.
Encryption
After the authentication step, other security measures are taken to protect the users' sensitive data from cybercrime. The data can be encrypted and transferred from the end-user to the application to keep the data secure from vulnerabilities. Providing end-to-end encryption within the applications is crucial to keep your application secure from all levels of threats. It is the top strategy used by IT professionals to secure data traffic.
Application security testing
Application security testing is a measure taken by the IT teams at the developing stage to ensure all the above measures work correctly on the application. The IT teams use several application security testing tools to identify all kinds of vulnerabilities in the application. Drogenide Softwares provides complete application security testing support for our clients to save their applications from all kinds of cyber threats.
IoT security
With the massive boom of the Internet of things in the market. There is a need to make IoT services secure. We are continuously adapting the latest trends in the industry to provide businesses with the best assistance with robust security. The biggest challenge to the companies to implement IoT services in their organizations is the threat of data loss. We at Drogenide Softwares, with our robust security methods, focus on making the IoT services safe and secure for the implementation of the organizations. Organizations need to be completely aware of the various IoT threats. The major IoT threats include:
- Botnets
- Denial of service
- Man-in-the-middle
- Identity and data theft
- Social engineering
- Advanced persistent threats
- Ransomware
- Remote recording





